Posted by: Aubrey Felix on August 14, 2024 at 10:19 am
Phishing scams are becoming more complicated. And, increasingly sophisticated. This makes it easy for even the most vigilant professionals to fall victim. One such prevalent scam involves fraudulent W9 forms and fake invoices. Let’s explore how these W9 phishing scams operate, how you can identify them, and steps to protect yourself and your organization.

Image by Pixabay
How W9 Phishing Scams Work
Phishing scams involving W9 forms typically start with an email that appears to come from a legitimate source. The email might include a request for sensitive information, such as taxpayer identification numbers, or an invoice for services supposedly rendered. These emails usually look convincing, complete with professional language and official-looking documents.
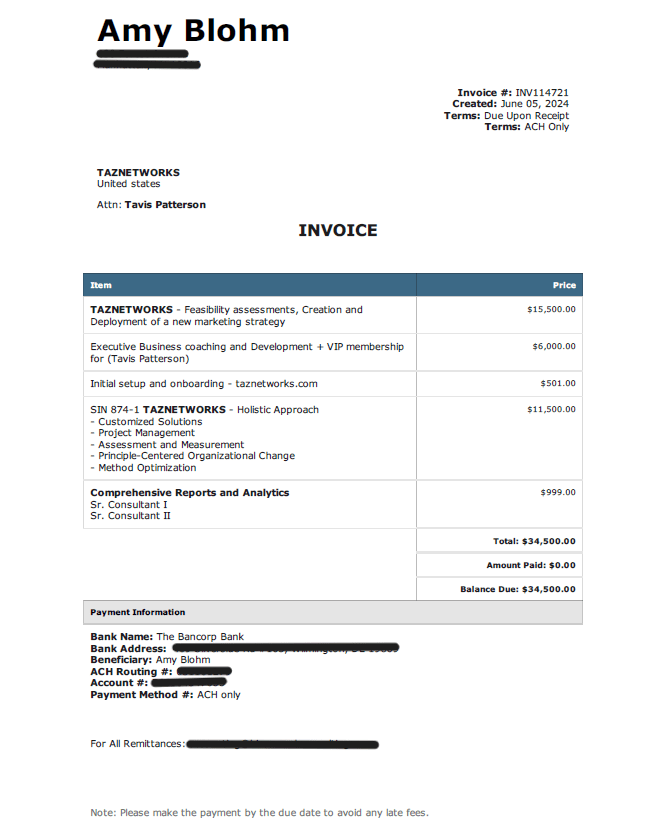
A recent example happened in our company. Which just illustrates how easy it is to be targeted by this scam. We received an invoice from someone claiming to be Amy Blohm, representing a company offering various business services. Along with this invoice, we received a completed W9 form to facilitate payment. Kudos to our accounting department for double checking and getting verbal confirmation before making the payment.
The scammer’s goal was to try and trick recipients into either paying a fake invoice or divulging sensitive information through the W9 form. Once the payment is made or information is shared, it becomes challenging to recover the funds or prevent further misuse of the information. (See example invoice below)
Identifying Phishing Scams
- Unsolicited Requests: Be wary of unexpected requests for payments or sensitive information, especially if they come from unfamiliar sources.
- Urgent Language: Phishing emails often use urgent or threatening language to prompt immediate action without verification.
- Check for Discrepancies: Examine the email and documents closely. Look for inconsistencies in email addresses, company names, and other details.
- Verify the Sender: Contact the supposed sender through a known, trusted method (e.g., phone call to their official number) to confirm the request’s legitimacy.
In our case, the invoice from “Amy Blohm” listed services that were never contracted by our company, a red flag that prompted further investigation.
Steps to Avoid Falling Victim
So, what do you do to prepare for this in your company? Here are some steps that can help you to stay protected.
- Educate Employees: Regularly train employees on recognizing phishing attempts and the importance of verifying requests.
- Implement Verification Processes: Establish a protocol for verifying the legitimacy of invoices and requests for sensitive information. This might include:
- Cross-checking requests with known contacts within the company.
- Using two-factor authentication for sensitive transactions.
- Get Verbal Confirmation: Always seek verbal confirmation before paying these large requests. Don’t hesitate to ask your boss if this is a purchase they approved of. Trust us, they would rather you ask them than be out of that money.
- Use Secure Communication Channels: Avoid sharing sensitive information over email. Use secure portals or encrypted communication channels whenever possible.
- Monitor Financial Transactions: Regularly review and monitor financial transactions to identify any unauthorized activities promptly.
Case Study: Our Experience
In our recent experience, we received an invoice for $34,500 for services that were never rendered. The invoice detailed various consulting and marketing services supposedly provided to TAZ Networks. The scammer also sent a W9 form to lend credibility to the request.
Upon receiving these documents, we:
- Cross-checked with our records and found no contract or agreement with the supposed service provider.
- Got verbal confirmation. Our accounting department checked with Tavis the owner of TAZ Networks. And sure enough, he had never heard of Amy Blohm.
- Confirmed that the request was fraudulent and took steps to report and block the scammer.
By taking these precautionary steps, we didn’t fall victim to this sophisticated scam.
Conclusion
The lesson is clear. W9 phishing scams are increasingly sophisticated, but with vigilance and robust verification processes, you can protect your small business. So keep educating your team, verify all requests, and always seek verbal confirmation before making any payments. Remember, it’s better to be cautious and take an extra step in verification than to fall victim to a scam.
By staying informed and implementing these measures, you can safeguard your small business against phishing attempts and maintain the integrity of your business. For more tips on protecting your business from scams, check out our IT Security Services and learn how TAZ Networks can help you safeguard your operations.
Contact TAZ Networks today