Posted by: TAZ Networks on September 30, 2016 at 4:22 pm
With thanks to Stacie Studer.
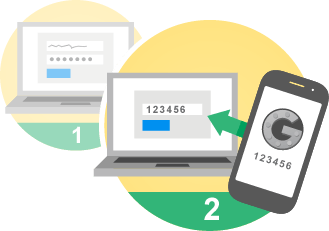
Two-step security, a.k.a. Multi-Function Authentication or MFA, adds another layer of protection to your accounts.
Have you heard of MFA or U2F? Both of these phrases relate to one thing… two-step security. We talk a lot about security around here because it really is a big deal. Do you want to avoid the hassle and risk of a serious security breach? Two-step security or Multi-Factor Authentication provides another layer of protection. It is simply adding a step in identifying yourself to the computer or website you are trying to access.
Setting up two-step security might be a pain at first, but think how secure you’ll feel when you get a text message saying, “Here’s your security code,” when you know you are not trying to log in. Having two-step security set up has just saved you a lot of time and aggravation by keeping the bad guys out of your system!
Some Two-Step Security Methods
SMS – With SMS authentication, you sign in and the web site sends a confirmation code to your phone via text message. Many consumer-level online services use this simple method for a basic level of additional security.
Email – With this method, the web site or service you are signing into sends the code to your email, which you must then enter. This is slightly more secure than SMS since, presumably, you also needed to enter at least a password to get into your email to get the code.
Third party – Services such as Authy will generate a random code for you to enter at login. This adds yet another layer of protection for your account.
These methods are not just for business! You can set up two-step security for your personal email, Facebook, etc.
Moving into big security, Universal 2nd Factor (U2F) adds another layer to two-step authentication. With U2F you use a USB key which needs to be plugged into any and every computer you want to log into. Sure you have to make sure to keep it on you (and not lose it), but what’s really nice is no password is required! Simply press the button on the USB and you’re in. These devices are typically referred to as tokens and are increasing in popularity. Soon these devices will not even have to be plugged in, they will simply work with Bluetooth or near-field wireless communication.
Can I Opt Out?
Resisting two-step authentication is futile at this point as many websites are now requiring it in some form. For example, here at TAZ Networks, our client documentation portal requires us to enter a randomly-generated code from a third party when we log in. Our main distributor emails us a similar code to protect our purchasing account.
We’re constantly working to stay on top of security; let us know if we can help you!