Posted by: TAZ Networks on August 3, 2018 at 8:00 am
Do you know why you keep getting those annoying phishing emails? Because they work. Maybe not on you, but for every one of those emails, someone, somewhere has clicked on it.
“Why?” you might ask. “Don’t people know how to identify a phishing attempt?”
While we feel your pain, the sad truth is that hackers use many of the same tactics as marketing companies. They play on people’s emotions. They test email subject lines to see which ones people fall for. And then they use those email subject lines over and over again.
It’s no longer easy to identify a spam email by the misspelled words and “Dear Mrs. Lady” intros. Hackers have gotten smarter and more sophisticated. They have learned how to imitate your boss, your social media accounts, and your bank. They use psychological tricks and language that sounds legitimate to get people to click.
And people – and businesses – fall victim to these emails every single day.
One way to protect yourself is to be familiar with the kinds of subject lines these scammers use. When you see them in your inbox, don’t just click the links, but use a little extra caution and some easy precautions, which we’ll list a little further down in this article.
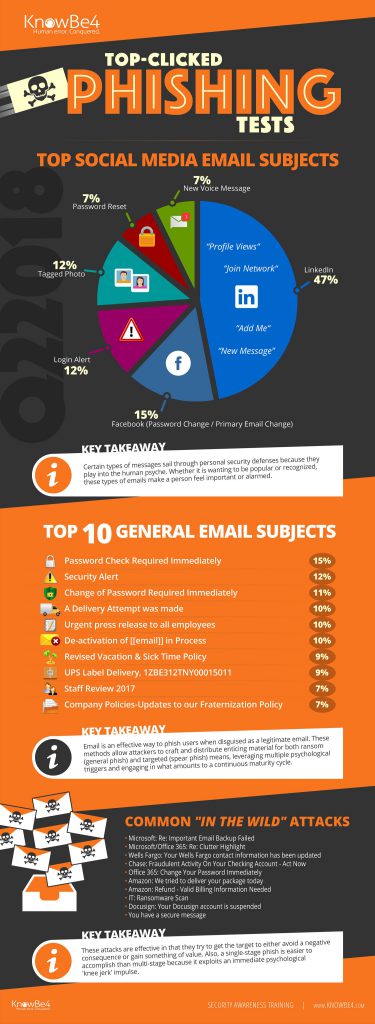
CyberheistNews tracks the most-clicked scam email subject lines every quarter. Here are some examples of the most effective common phishing email subject lines:
- Wells Fargo: Your Wells Fargo contact information has been updated
- Chase: Fraudulent Activity On Your Checking Account – Act Now
- Amazon: We tried to deliver your package today
- UPS Label Delivery, 1ZBE312TNY00015011
- Change of Password Required Immediately
(See the infographic for more.)
How to Protect Yourself From Common Phishing Email Scams
Clearly, the most common phishing email subject lines are designed to prey upon your need for friendship, your curiosity, and your need to keep your job. So, how can you protect yourself from these emails?
- Prevention. Solid anti-spam and spam filtering software will keep most of these emails from ever hitting your inbox. A well-configured firewall can block spam from ever hitting your network. A filtering product sends suspicious messages to a quarantine. (Microsoft 365 has spam filtering built right in.) Users can quickly skim the subject lines for anything that seems legitimate. (From our own and our clients’ experience, we can tell you that 80%-90% of the email in this quarantine is either a scam or spam and safely ignored.)
- Be skeptical. Are you expecting an Amazon package? Do you even bank with Chase? Even if the email links claim to be from accounts you actually have, a little caution is in order. Best to open a fresh web browser page and log into your account from there. Clicking the link in the email and logging in there can hand over your credentials to the scammers.
- Policies. Yes, policies. Decision-makers need to set policies in place for handling items like personal information, financial wire transfers, or gift card purchases. A single email request should not be enough; requests should be double-verified with a phone call or face-to-face conversation. Set up these policies even if these processes are things your company does regularly!
As hackers and scammers get more and more sophisticated, it can be difficult to tell the difference between a scam email and a legitimate-yet-unusual one. Getting familiar with the basics of scam emails, what they look like, and how they work can be a good workplace security practice.